[vc_row][vc_column][vc_column_text]With the increased sophistication of cyberattacks, it has become critical for businesses to protect their information at all costs. As cybersecurity methods continuously evolve, endpoint detection and response (EDR) should remain in your tech solution toolbox. If you aren’t sure about EDR and its effectiveness, this blog will provide knowledge on this instrumental key for optimal business health.
What is EDR and Why You Need It
Endpoint Detection (EDR) is a term coined by former Gartner tech specialist Anton Chuvakin in 2013. Simply put, EDR is an emergency security system that can both detect and investigate suspicious activity on hosts and endpoints like laptops, desktops, phones, etc. Also known as the “central component of modern endpoint security” by Cynet, it is a quick way to help security teams quickly identify and respond to potential threats.
EDR has gained popularity as businesses are switching to cloud computing. Its current growth rate of 26% shows that EDR will become a necessary component for all business cybersecurity plans. Unlike other cybersecurity methods, endpoint detection sends automatic responses to the identified threat to remove or contain them. In addition, EDR uses both forensics and analysis tools to research identity threats and other suspicious activity that could threaten business security.
EDR vs. MDR: Which One Do You Need?
As EDR is gaining traction within the technology security industry, MDR has become a topic of conversation. MDR, or Managed Endpoint Detection and Response, is a security service offering that includes endpoint detection tools. Rather than taking EDR matters into your own hands, MDR allows you to let experts like those at ABI handle your tech needs. This allows you to focus more energy on pushing your mission forward. You can learn more about our MDR services here.
“EDR is a tool that is deployed to protect a particular endpoint, while MDR is a service that provides security monitoring and management across an organization’s entire IT environment.” – Cynet
How Does EDR Security Work
EDR has valuable tools and systems to keep your business running smoothly 24/7. Although it is not a replacement for other cybersecurity measures, it is another valuable addition that can bring an extra layer of protection to your organization.
Here is how the process works:
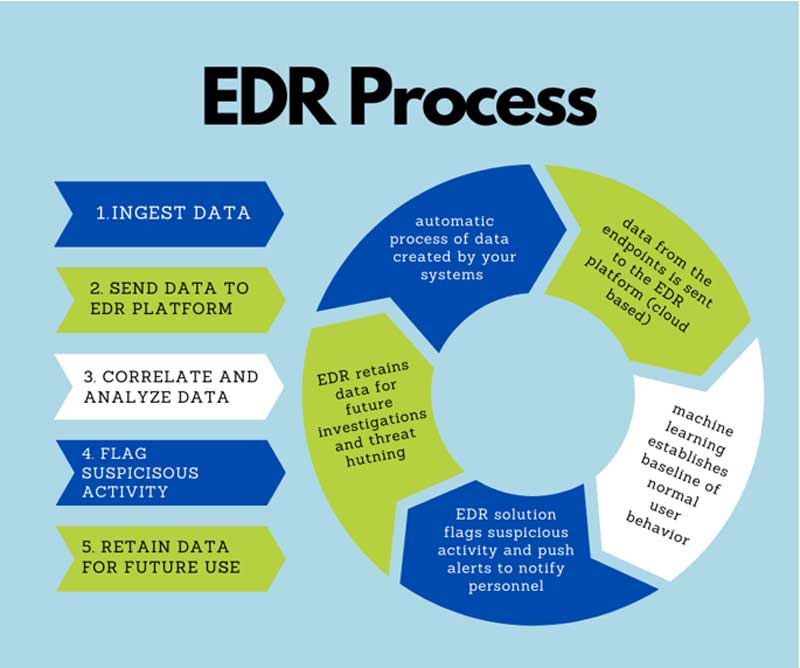
While the implementation of EDR may seem intense, these tools bring about reduced risk and lowered costs. Some of these key EDR tools include
- Insights – EDR has advanced AI algorithms to automate the threat identification and alerting process
- Response – The response features help your operators, whether in-house or through a provider like ABI, immediately investigate the issue. They use past information from suspected endpoints and present information from the live system memory to determine patterns.
- Forensics – The added forensics data helps track threats and similar activities that might have been missed. It also establishes a clear timeline of the attack and identifies affected systems before a breach can occur.
- Automation – When a threat is detected, EDR tools automatically stop or disconnect any compromised endpoints and alert the necessary parties.
With this around-the-clock monitoring, you can rest assured that your business is safe for at-home work and nationwide expansion.
Protect Your Business with Effective EDR Security
Without implementing an EDR solution in your cybersecurity plan, your business could be at a higher risk of losing important documents and, in turn, your reputation. With more than 20 years of experience in the tech industry, ABI has the expertise to help you pursue suitable security options for your business.
Not sure where to begin with tech solutions for your business? ABI offers the best defense against network attacks in Canoga Park and the San Fernando Valley with our Managed Detection & Response Services.
We also offer other IT services that include:
- Managed IT Services
- Backup & Recovery
- Cloud Solutions
- Microsoft 365
- Email Spam, Phishing & Virus Protection
- Network Support
- Work from Home Solutions for Employees
- Network & Cybersecurity
- Data Center
- Business Phone Systems
- Business Security Cameras
Ready to up your cyber security game? ABI’s client-focused solutions are proven to bring results. Schedule a free consultation with us to get started.[/vc_column_text][/vc_column][/vc_row]